
On a server if you have a rkhunter running and you suddenly you get some weird Warnings for suspicious files under dev, like show in in the screenshot and you're puzzled how comes this happened as so far it was not reported before the regular package patching update conducted …
root@haproxy-server ~]# rkhunter –check
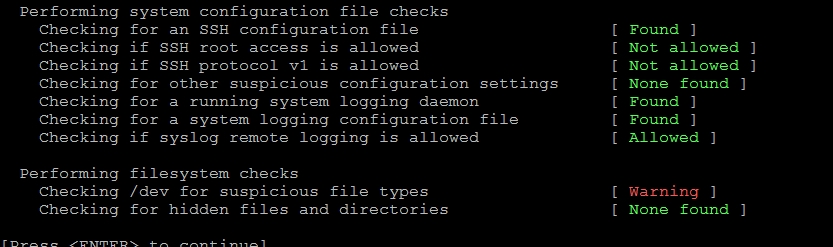
To investigate further I've checked rkhunter produced log /var/log/rkhunter.log for a verobose message and found more specifics there on what is the exact files which rkhunter finds suspicious.
To further investigate what exactly are this suspicious files for or where, they're used for something on the system or in reality it is a hacker who hacked our supposibly PCI compliant system, I've used the good old fuser command which is capable to show which system process is actively using a file. To have fuser report for each file from /var/log/rkhunter.log with below shell loop:
[root@haproxy-server ~]# for i in $(tail -n 50 /var/log/rkhunter/rkhunter.log|grep -i /dev/shm|awk '{ print $2 }'|sed -e 's#:##g'); do fuser -v $i; done
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1851-27-f1sTlC/qb-request-cpg-header:
root 1783 ….m corosync
hacluster 1851 ….m attrd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-event-quorum-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-event-quorum-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-response-quorum-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-response-quorum-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-request-quorum-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-26-Znk1UM/qb-request-quorum-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-event-cpg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-event-cpg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-response-cpg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-response-cpg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-request-cpg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-25-oCdaKX/qb-request-cpg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-event-cfg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-event-cfg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-response-cfg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-response-cfg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-request-cfg-data:
root 1783 ….m corosync
root 1844 ….m pacemakerd
BEN. PID ZUGR. BEFEHL
/dev/shm/qb-1783-1844-24-GKyj3l/qb-request-cfg-header:
root 1783 ….m corosync
root 1844 ….m pacemakerd
As you see from the output all the /dev/shm/qb/ files in question are currently opened by the corosync / pacemaker and necessery for proper work of the haproxy cluster processes running on the machines.
How to solve the /dev/ suspcisios files rkhunter warning?
To solve we need to tell rkhunter not check against this files this is done via /etc/rkhunter.conf first I thought this is done by EXISTWHITELIST= but then it seems there is a special option for rkhunter whitelisting /dev type of files only ALLOWDEVFILE.
Hence to resolve the warning for the upcoming planned early PCI audit and save us troubles we had to add on running OS which is CentOS Linux release 7.8.2003 (Core) in /etc/rkhunter.conf
ALLOWDEVFILE=/dev/shm/qb-*/qb-*
Re-run
# rkhunter –check
and Voila, the warning should be no more.
Another thing is on another machine the warnings produced by rkhunter were a bit different as rkhunter has mistakenly detected the root login is enabled where in reality PermitRootLogin was set to no in /etc/ssh/sshd_config
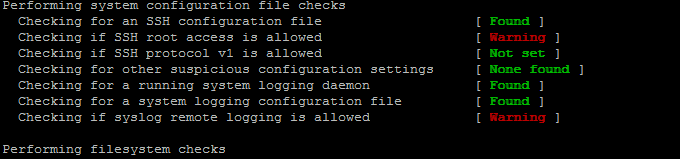
As the problem was experienced on some machines and on others it was not.
I've done the standard boringconfig comparison we sysadmins do to tell
why stuff differs.
The result was on first machine where we had everything working as expected and
PermitRootLogin no was recognized the correct configuration was:
— SNAP —
#ALLOW_SSH_ROOT_USER=no
ALLOW_SSH_ROOT_USER=unset
— END —
On the second server where the problem was experienced the values was:
— SNAP —
#ALLOW_SSH_ROOT_USER=unset
ALLOW_SSH_ROOT_USER=no
— END —
Note that, the warning produced regarding the rsyslog remote logging is allowed is perfectly fine as, we had enabled remote logging to a central log server on the machines, this is done with:
This is done with config options under /etc/rsyslog.conf
# Configure Remote rsyslog logging server
*.* @remote-logging-server.com:514
*.* @remote-logging-server.com:514
More helpful Articles

Tags: access, BEFEHL, BEN, checking, config options, fix, How to, rkhunter, shm, ssh







